It's All About the How
We've Been in Your Shoes
As a reliable and trustworthy service provider for CMMC, VLC can be your one true ally in ensuring that all your cyber-maturity needs are fully met.
Cybersecurity Maturity Model Certification (CMMC) is a prerequisite for all organizations in the supply chain to the United States Department of Defense (DoD). This includes a prime contractor, sub-contractor, or sub-tier supplier. CMMC guarantees that an organization has reached the minimum point of cybersecurity needed to be commissioned with the classes of data they obtain or control. It is a distinct necessity for the current DoD contractors, substituting the self-attestation model and shifting to self-governing third-party certification.
CMMC is configuring swiftly, with the latest releases evolving constantly. If you consider that you require CMMC certification or looking forward to get off the ground on preparing for certification, contact us at the earliest.
CMMC 2.0
- Protect vulnerable data.
- Powerfully improve Defense Industrial Base (DIB) cybersecurity to counteract the emerging threats.
- Offer full responsibility while cutting down hindrances to compliance with DoD conditions.
- Make efforts towards fabricating a collaborative ecosystem of cybersecurity and cyber stability.
- Strengthen public trust via enhanced skills and ethical measures.
Fundamental Features of CMMC 2.0
An Enhanced Version
- Concentrative on the essential demands: Streamlines and compiles the CMMC model from the earlier five to only three compliance levels.
- Adheres to the necessary standards: Operates on the National Institute of Standards and Technology (NIST) cybersecurity norms.
Trustworthy Evaluations
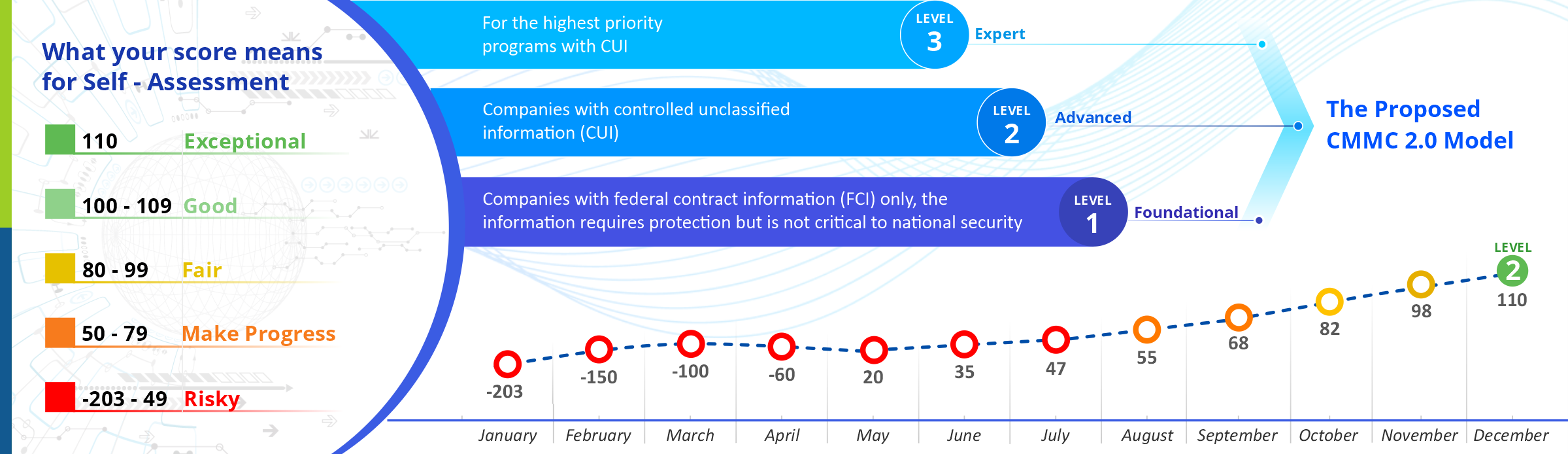
- Lowered assessment charges: Enables all businesses at Level 1 (Foundational) and a few companies at Level 2 (Advanced) to exhibit compliance via self-assessments.
- Increased accountability: Boosts the supervision of professional and ethical standards of third-party auditors.
Agile Implementation
- Cooperative values: Under some restricted conditions, businesses are allowed to make Plans of Action & Milestones (POA&Ms) to earn certification.
- Extra flexibility & Speed: Facilitates waivers to CMMC provisions in certain restricted occasions.
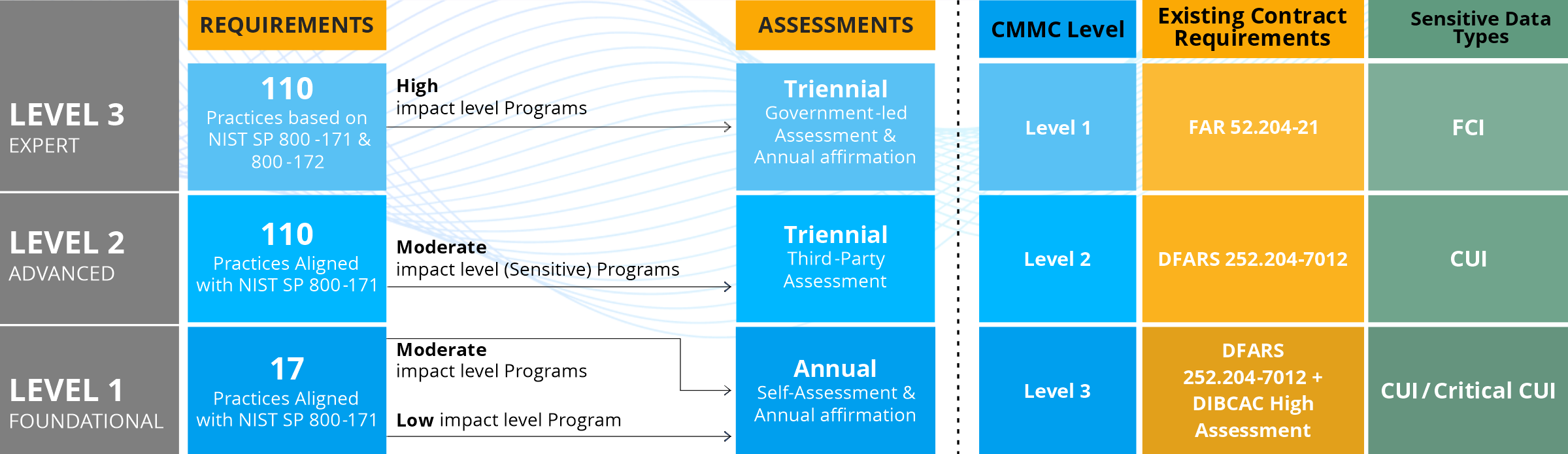
- Self-Assessment, Self-Attestation: This is for Level 1 and non-prioritized Level 2 procurements.
- Independent Third Party (C3PAO) Assessment: This assessment is for prioritized Level 2 procurements.
- C3PAO and Government Assessment: Level 3 assessments will be performed to the Level 2 baseline by a C3PAO, and the DoD shall assess the rest of the requirements.
The certification shall be premised on the present needs such as NIST SP 800-171, NIST SP 800-53, private sector offerings, and pertinent information from academic communities.
VLC’s CMMC Compliance Services
MSSP and CMMC Defense Monitoring
VLC Solutions MSSP services can satisfy CMMC auditing and registering essentials. We can also assist in each anticipated CMMC audit compliance ambitions when concluded.
CMMC Penetration Testing
CMMC acquires most of the necessary controls from NIST, and it has always needed penetration testing. This specification stretches past a programmed vulnerability screening. Penetration testing is organized and conducted by penetration test operators and units with essential abilities and expertise. VLC's teams have specialized knowledge in operating systems, application-level defense, and network management.
CMMC Establishment, Progress, and Documentation of System Security Plans (SSP)
The expansion of a CMMC System Security Plan (SSP) can feel challenging. If you're looking for articulate assistance concerning System Security Plans (SSP) and Plan of Action and Milestones (POA&M), please feel free to Contact US.
CMMC Preparedness Assessment
If you’re contemplating to kick-start on arranging for CMMC compliance, a judicious point of beginning is a CMMC Cybersecurity Preparedness Assessment. This exercise will gauge your current position and the standard protocol needed to provide for the imminent corroboration.
Comprehensive CMMC Assistance and Consulting
The CMMC fundamentals are advancing consistently. No matter what your CMMC needs are, VLC Solutions can attend and ensure extensive cybersecurity, compliance services and can viably be trusted in aiding your certification preparation. Irrespective of your prevailing status in this realm, we can vouch to help you attain the ultimate goals you have in mind for your business.
CMMC Gap Analysis
GAP analysis is your first step in readying for CMMC compliance. VLC will help you conduct a formal gap analysis with all 110 controls in NIST SP 800-171 and research your readiness to complete CMMC compliance needs.
Based on your organization's structure and design, we will conduct the compliance review onsite or remotely. After finishing the CMMC gap analysis, we deliver a detailed checklist of all the action items required to attain your preferred level of compliance. Furthermore, we will have an executive-level briefing discoursing essential concern.
CMMC System Security Plan (Policies & Procedures) Engagement
For organizations with stronger IT understanding, we will work with their stakeholders to address the compliance documentation, procedures, and strategies while executing the CMMC practices. The System Security Plan (SSP) Engagement contains writing and keeping the CMMC SSP Plan along with POA&M based on the organization’s infrastructure to isolate Controlled Unclassified Information (CUI). We document policies and procedures for the protection of FCI and CUI across the business, including quarterly and annual updates.
Assured Defense – Managed Security Support Plan
We handle and execute any part of your CMMC compliance transition for companies needing a more hands-on technique. Our Assured Defense Plan is a menu-style offering where you choose what services work most suitably for your needs. This plan delivers solutions and outlines a POA&M to monitor the progress. VLC's team will develop and sustain your SSP policies and procedures with monthly and quarterly updates to satisfy the NIST SP 800-171 and CMMC compliance necessities. Also, our constant tracking will contain audit assessments, vulnerability management, anti-malware / firewall monitoring and management, and web filtering. As and when needed, we shall execute and configure the required hardware and software to satisfy CMMC compliance.
What stage of CMMC are you at?
VLC is one of the best candidates for the CMMC readiness assessment and preparedness. Irrespective of where you're from on your compliance path, our CMMC consulting and appraisal solutions can help you proficiently plan and prepare for your CMMC Certification.
FAQ's
DIB contractors hold and utilize sensitive government data to create and provide goods and services. The CMMC works to make sure that they secure this data in the same way that the military and other government organizations do.
For many years, the U.S. government gave cybersecurity advice to contractors, but there was no mechanism for the contractors to demonstrate the effectiveness of their cybersecurity programs. Outside assessors conduct a new set of certifications from CMMC. Before receiving future government contracts, contractors must get certified.
CMMC now covers only DoD contractors, and the DoD is starting to demand certification for some contracts. Future CMMC applications could include all non-DoD federal contractors.
CUI is data that the government or contractor generates or owns and that must be protected by law, rule, or policy at all levels of government. CUI information must only be managed with the right security measures in place.
The terms and conditions of DoD procurement contracts are described in DFARS. DFARS clauses that subject contractors to CMMC obligations are built upon by CMMC.
The DOD along with CyberAB has accredited and authorized C3PAO to carry out CMMC evaluations. CMMC certificates are issued by the C3PAO based on the findings of the evaluations.
